Cisco 8000 - Platform Security
Cisco 8000 - Platform Security
Introduction
Networking is evolving at a formidable pace, it is fundamentally transforming every networking segment. The main driver behind this change is the rising tide of data generated by ever increasing number of users, devices and applications. To address network growth at these unprecedented levels operators around the world are considering various architectural options with emphasis on scale, latency, resiliency, automation and security. As they expand their networks and have tighter control over the network resources to better serve their customers security has taken center stage. Security is important because a network is an attack surface for cyberattacks. As networks continue to expand in response to changing networking landscape, they are increasingly vulnerable to cyberattacks which are a major threat for the operators. Securing underlying infrastructure is no longer merely desired by operators, it is a key requirement for a secure network.
This white paper outlines the platform security features that are built into Cisco 8000 platform. It highlights how security is addressed throughout the entire life cycle of the product. Furthermore, it describes how security is built into the platform, what type of security features are introduced and how do they mitigate security risks.
Networks & Cyberattacks
For years Cisco has been warning of increased cybercriminal activity at the global level. In its 2018 Annual Cybersecurity Report Cisco states that cyberattacks are more sophisticated in nature exerting bigger business and financial impact. Technologies used for normal business operations such as the internet and the cloud are being increasingly targeted by cybercriminals. Their most significant target is exploitation of gaps created by network expansion. Furthermore, the report points out that the supply chain attacks are on the rise as well with increasing complexity. Their impact can be quite massive and remain undetected for a long period of time. To curb supply chain attacks, it is recommended to work with vendors who issue Common Vulnerabilities and Exposures (CVE) reports, have a comprehensive supply/value chain security program to protect their systems from compromise, and are capable of quickly addressing any system level vulnerabilities[1].
There are many notable recent incidences of cyber breaches resulting in enormous damages. Hackers exploited software vulnerabilities and were able to steal millions of dollars, permanently erase computer data and maliciously hack into corporate networks to steal valuable consumer information [7]. Cybercriminals have exploited supply chain vulnerabilities to replace hardware or software. Attackers are reported to have successfully attacked the supply chains of different companies altering hardware during the manufacturing process gaining access to valuable data [10, 11]. These articles underscore a key point that supply chain attacks are more likely and more frequently to happen given the global nature of product development.
Cisco’s Report
According to Cisco’s Annual Cybersecurity Report, economic losses as a result of cyberattacks are real. Attacks take months or years to detect and resolve. Cisco’s 2018 Security Capabilities Benchmark study revealed that more than half (53%) of all attacks resulted in financial damages of more than $500,000. Furthermore, the extent of damages is far beyond financial; businesses have lost their revenue, customers, partners, ability to capture new opportunities, incurred avoidable operational cost, etc. [1].
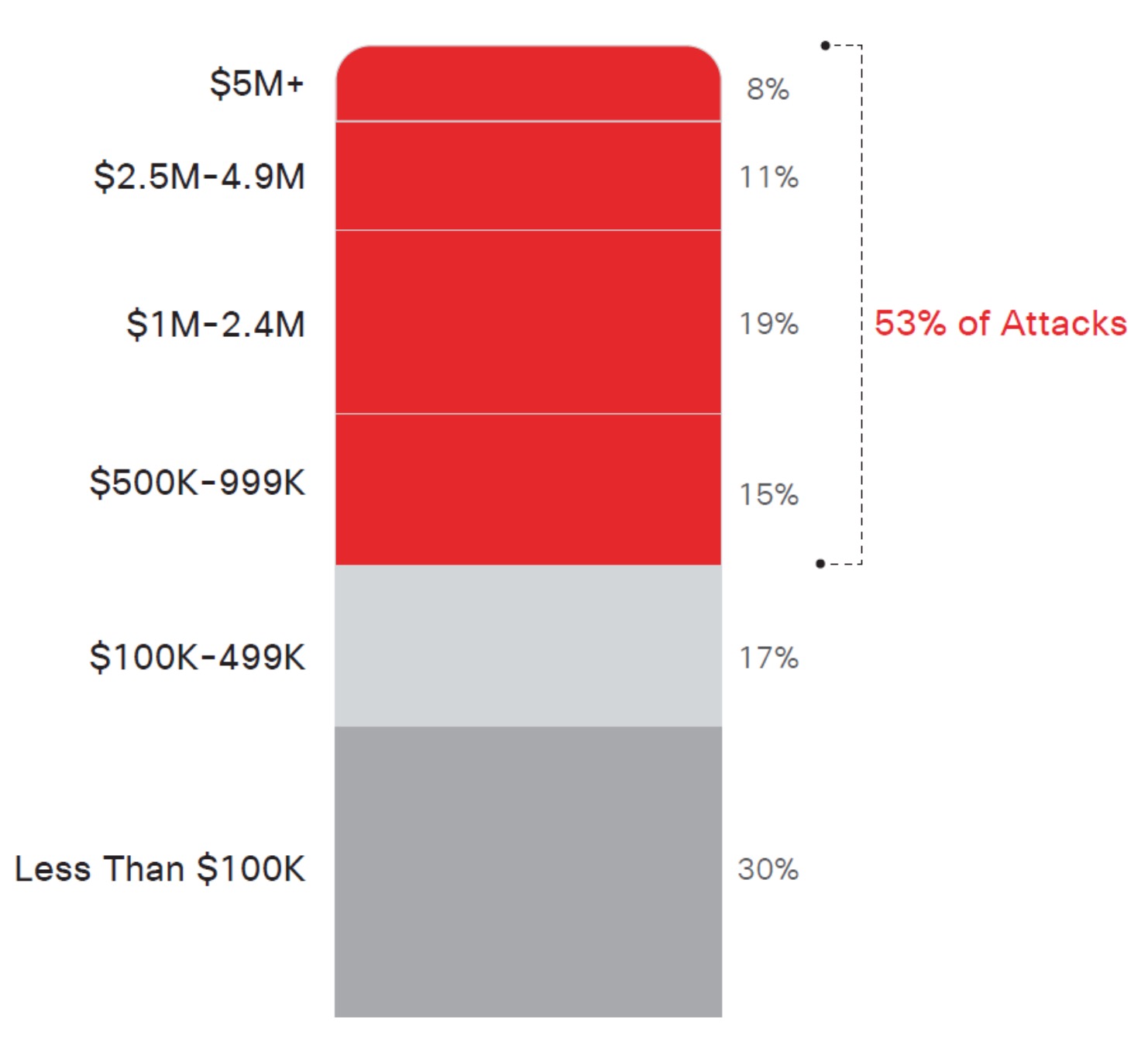
Figure 1 Cyber-attack damages (Source: Cisco 2018 Security Capabilities Benchmark Sturdy)
Global Trends
With current advances in IoT and availability of network infrastructure, more devices are going online. As per Cisco’s Visual Network Index (VNI) forecast, by the year 2022 there will be 4.8 Billion global internet users. There will be around 26 Billion network devices connected with 82% of video traffic over the network [2].

Figure 2 Global Internet Growths and Trends
In addition, there will be 2 Billion BYOD (Bring Your Own Device) in the workplace by the year 2020 as per Mindcommerce. As networks continue to expand, it is becoming increasingly difficult to detect the security attacks and take timely corrective measures. The average industry breach time-to-detection is 191 days.
By 2020, more than half of all devices and connections will be machine-to-machine, up from 34% in 2017. That’s 14.6 billion connections from smart speakers, fixtures, devices and everything else, up from 6.1 billion. Video, gaming and multimedia will make up more than 85% of all traffic [3].
IP video traffic will quadruple by 2022. As a result, it will make up an even larger percentage of total IP traffic than before—up to 82% from 75%.
Gaming traffic is expected to grow nine-fold from 2017 to 2022. It will represent 4% of overall IP traffic in 2022.
Virtual and augmented reality traffic will skyrocket as more consumers and businesses use the technologies. By 2022, virtual and augmented reality traffic will reach 4.02 Exabyte / month, up from 0.33 Exabyte / month in 2017.
Trustworthy Networks
For the above scale of data, it will be challenging to build secure and trustworthy network unless the platform hardware is built to handle and circumvent the threats and attacks. Trust is a new dimension in security that focuses on maintaining the hardware and software integrity in the network.
Trustworthy networks are built with devices that have security embedded throughout their product lifecycle and are resilient against today’s sophisticated attacks. Trustworthy networks are designed with foundational security capabilities that verify devices for authenticity and integrity which provides evidence that network devices are operating as intended. Similar to Design For Testability (DFT) and Design For Manufacturability (DFM), Cisco platform products are designed from concept to production based on Cisco trustworthy framework. Cisco has led the industry in this development approach for many years using Cisco Secure Development Lifecycle and the 8000 series is leveraging the same best practices using this proven methodology.
Trust features are built in to every stage of product development at Cisco right from component ordering through a trusted supply chain network to downloading the boot image, shipping the final product to the customer and customer deployment or field deployment.
Uncompromised Network Security
Cisco has a long history of offering industry leading security offerings and it is the biggest cybersecurity vendor in the world based on revenue – and the second fastest growing. Canalys Research recently ranked the top 5 vendors, with Cisco leading the pack at just under 10% market share (as of Q4 2018) [8].

Figure 3 Top Five Cybersecurity Vendors
Cisco products provide uncompromised network security which is designed to protect the usability and integrity of network and data; it includes both hardware and software technologies. Effective network security manages access to the network and it targets a variety of threats and stops them from entering or spreading on the network.
Platform security has been a key strategic product development requirement at Cisco. Cisco believes that a strong platform security is a keystone of a powerful secure network. Therefore, a complete platform lifecycle security approach is used in developing products at Cisco. It starts right from the product concept to product End of Life (EoL). This includes, considering hardware design, software design, system architecture and partner eco system including silicon vendors and manufacturing partners.
Cisco Trustworthy Framework
As networks continue to evolve so does the cyber-security landscape. Cisco has been responding to this growing threat with a holistic approach with Cisco trustworthy® framework. This framework addresses security at every phase of a product’s lifecycle from concept to end of life. It starts with a product deployment model and typical use cases. The framework explores the following concepts [13]:
What is product’s threat model?
What attack vectors are specific to this product?
What measures can be taken to make this product robust and threat resistant?
What is product’s security operational model?
What type security measures need to be provisioned for example pre-boot, post- boot, runtime and supply chain security?
A critical step in designing secure and resilient networking solutions is to design hardware from the outset with embedded security features. The Cisco Trust Anchor Module (TAm) is a chip that implements a number of security features in a standards-based way. The Trust Anchor Module and other trustworthy technologies are used to enable following security features in the Cisco 8000 platform.
The Trust Anchor Module is used to enable following security features in Cisco 8000 platform:
Secure boot
Image signing
Runtime defenses
Supply chain security (Cisco Chip Protection)
Cisco Trust Anchor Module (TAm)
Platform identity is the first step in establishing platform security, it is done using Cisco Trust Anchor Module (TAm). TAm is a passive silicon module that connects to the CPU in a device. TAm is similar to Trusted Platform Module (TPM) by the Trusted Computing Group (TCG) which was accepted as a standard by ISO and IEC in 2009. TAm / TPM capabilities and common features are highlighted in Fig 4.
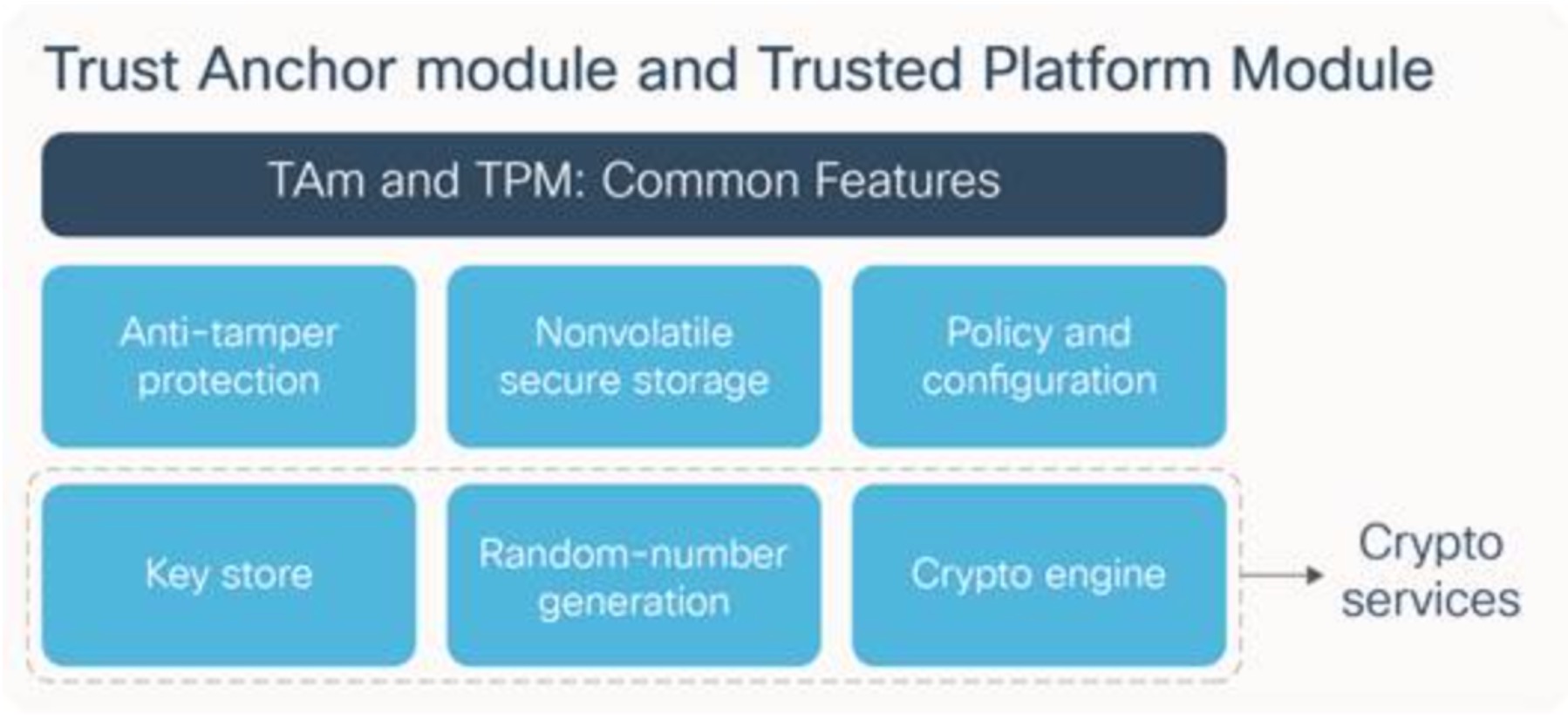
Figure 4 Cisco Trust Anchor Module and Trusted Platform Module
Originally developed to protect against counterfeiting and supply chain attacks, the Trust Anchor Module is a tamper-resistant chip that provides secure onchip storage, random number generation (RNG) for encryption, and a secure unique device identity for authentication.
During manufacturing phase, device identification is programmed into the TAm. This is done with Secure Unique Device Identification (SUDI) certificate. SUDI is an extension of device identity as defined by IEEE 802.1 working group. 802.1 AR standard defines a secure device identifier (DevID) as a cryptographic identity that is bound to a device and used to assert device identity. SUDI is permanently programmed into the TAm and logged by Cisco manufacturing server during system manufacturing and it is used for device authentication purposes. SUDI is an X.509 certificate which is globally unique per device. Cisco has a secure business-to-business network with its silicon, software and manufacturing partners. During manufacturing, critical system information such as SUDI is exchanged between suppliers and the Cisco back end process.
Cisco Secure Boot and UEFI Secure Boot
The hardware-anchored Secure Boot process is designed to ensure that only genuine, unmodified code is allowed to boot on the Cisco 8000 platform. It is anchored in hardware via TAm, thus providing a very robust security framework as shown in Fig.5. With the establishment of root of trust, secure boot monitors all stages of the boot process.
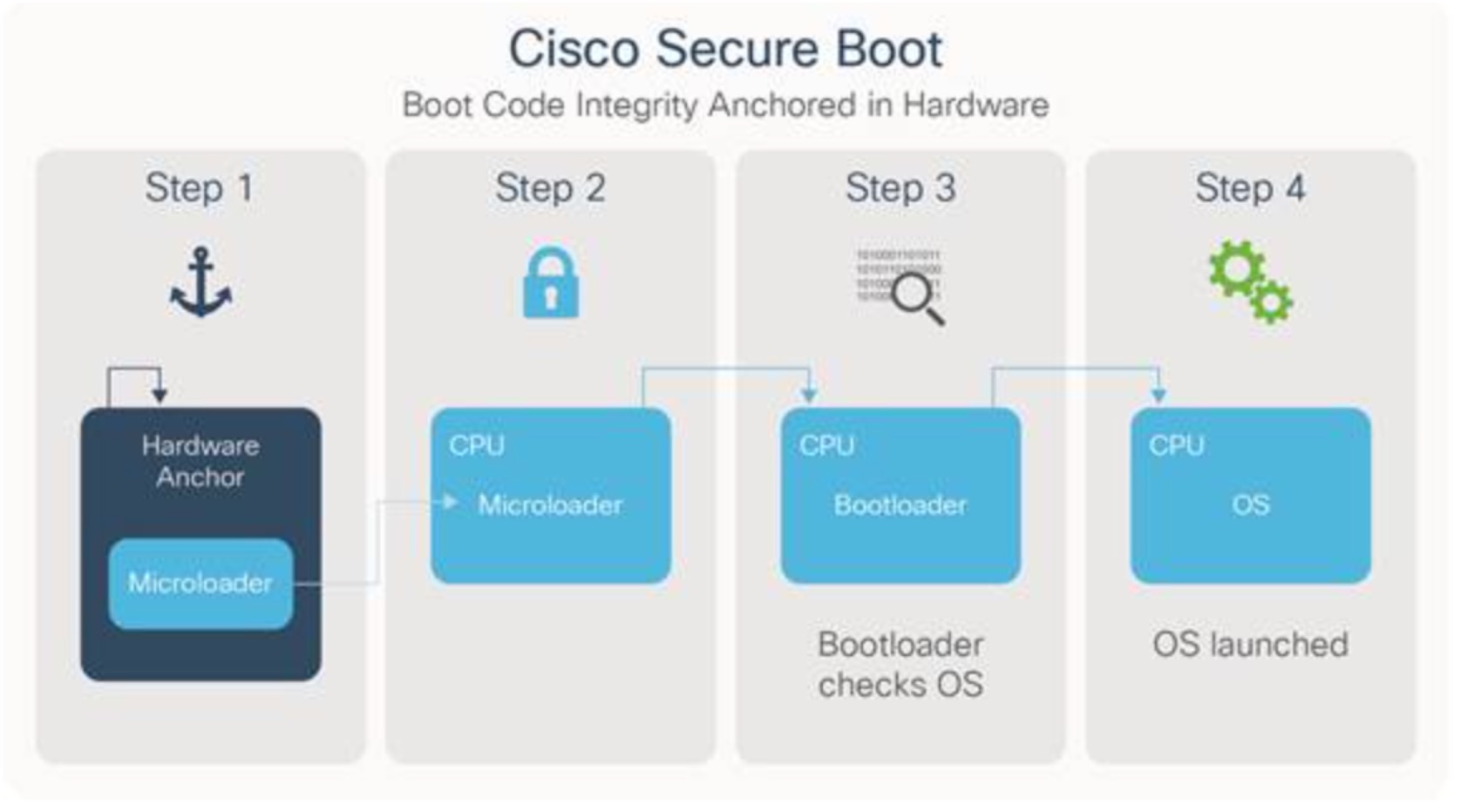
Figure 5 Cisco Secure Boot Process
It first authenticates a micro-loader, which is encrypted and signed by Cisco private keys, and stored in TAm. When the device boots, the micro-loader authenticates boot loader by validating its Cisco digital signature. Next, the bootloader authenticates the operating system (OS) by checking its digital signature.
This process creates a “chain of trust” from micro-loader through bootloader to the operating system, establishing the software authenticity and integrity. All these signatures are verified using keys that are securely stored in TAm at manufacturing time. This insures that software and hardware authenticity is verified during boot time leaving no room for hardware and / or software counterfeiting. If any digital signature checks fail, the Cisco device will not allow the software to boot.
Extending the Trust to run time application
After the verification of all the steps in the boot sequence, it is crucial to extend the integrity verification to run time application, Integrity Measurement Architecture (IMA) is intended to provide assurance that executables preparing to load have not been modified from their original form. IMA maintains a runtime measurement list and anchored in the TAm, an aggregate integrity value over this list. The benefit of anchoring the aggregate integrity value in the TAm is that the measurement list cannot be compromised by any software attack, without being detectable. Hence, on a trusted boot system, IMA can be used to attest to the system’s runtime integrity. The IMA- appraisal extension adds local integrity validation and enforcement of the measurement against a “good” value stored as an extended attribute. The method for validating the extended attributes provides file data integrity and authenticity.
IMA can work in 2 modes:
- Logging mode – In this mode, the system will log a message if the appraisal failed.
- Appraisal mode – In this mode the system will block applications if the appraisal failed.
The IMA signatures for all applications will be included in the RPM XR packages.
Secure JTAG
JTAG refers to IEEE 1149.1, Standard Test Access Port and Boundary Scan Architecture. IEEE 1149.1 compliant silicon devices may be connected together on a PCB to form a scan chain which is typically driven by external test equipment or debugger. The original application for JTAG was to be used by manufacturing to detect both structural and functional faults in the PCBA (Printed Circuit Board Assembly) to improve quality.

Figure 6 Board Level JTAG Chain
Most embedded devices provide a JTAG interface for debugging purposes. However, if left unprotected, this interface can become an important attack vector on the system. JTAG has also been adopted to program FPGAs and provide a CPU debug access port. Most CPU vendors including Intel, Freescale, Marvell, and AMD, allow for a debugger to be connected to the CPU’s JTAG port to assist with code debugging. It is the use of JTAG to provide a CPU debug access port that presents a security risk.
A laptop and a JTAG debugger is often all that is required to provide access to an embedded CPU allowing for retrieval of firmware images, dumping memory, and monitoring software execution. Small size coupled with a sophisticated tool set gives attackers a portable and yet powerful means to exploit a system. Potentially malicious uses of JTAG include:
- Intellectual Property Theft
- It is easier to reverse engineer than perform static binary analysis
- Counterfeiting
- Reverse engineering of anti-counterfeit mitigations and licensing schemes
- Modification of firmware to circumvent licensing
- Embed Malware
- Can be performed statically or dynamically
- Dynamic can evade image signing
- Theft of Secrets
- Private or symmetric cryptographic keys can be retrieved from memory
- Passwords retrieved from memory
Many of the threats listed above have been seen in network devices including Cisco products. CounterfeitCiscoproductshavebeenexaminedandfoundtocontainmodifiedsoftware images designed to circumvent protections. While the exact tools and techniques of real-world attacks are often unknown, JTAG makes it significantly easier to reverse engineer, modify and test software. Further confirming JTAG as desirable attack surface, a proof-of-concept attack was demonstrated by a German university team who used the JTAG interface on Cisco routers to monitor memory during run-time operation to extract private information.
The Cisco IP Secure JTAG monitor and strobe function is a specialized logic block designed to prevent the use of JTAG debuggers to probe and modify CPU memory contents. Secure JTAG both monitors the JTAG bus for activity and also periodically checks the continuity of the JTAG chain during run time operation. When unauthorized activity is detected or the JTAG chain integrity is compromised, the host system is notified, and corrective action is taken by the host.
Cisco Chip Protection
Attacks on supply chain may replace CPUs, ASICs with CPUs/ASICs containing Trojan/malware while the products are en route to the customers. Some have theorized that agencies are able to influence vendors of CPUs/ASICs to get them to put Trojans onto chips while others have theorized a Trojan in the form of an added silicon on board assembly. Cisco Chip Protection helps mitigate this threat with the use of unique identifiers stored inside the TAm device as a way to identify and track components through the lifecycle of products.
Cisco Chip Protection is applicable to all field replaceable units (FRUs). There is no “chassis level” chip validation feature. Imprint DB is a master copy in the TAm that stores the unique IDs of Cisco ASICs, CPUs/SOCs and other devices with their device types specific to a board. In most cases, unique ID is device serial number or appropriate value of that device. Imprint DB is a known good values database specific to a board. This is programmed on to a TAm device during the manufacturing process.
Some of the components measured are:
- CPUs
- ASICs
- SOCs
Observed DB is collected by firmware every time the board is booted and extended to the TAm device. If some measurements are not available through firmware, those needs to be collected immediately after those measurements are available from operating system drivers. It is an indication of a breach, if the observed DB does not match the imprint DB. This breach will result in an RMA.
Conclusion
Cybersecurity is a growing and sustaining challenge for Service Providers across the globe. Cisco has taken unprecedented steps to address this challenge using its trustworthy framework. Platform security is the cornerstone of Cisco’s security strategy. Cisco 8000 feature portfolio includes all the security features presented in this white paper. With these Built-in-Security features, Cisco 8000 family is ready to circumvent security threats keeping the network safe and secure.
References
- Cisco 2018 Annual Cybersecurity Report
- Cisco VNI Forecast
- Mindcommerce
- 2017 Cost of Data Breach Study Benchmark research sponsored by IBM Security Independently conducted by Ponemon Institute LLCJune 2017
- Cisco News Release Nov 27, 2018
- Cisco Built-in-Trust
- South China Morning Post: https://www.scmp.com/news/asia/east- asia/article/2163130/us-charge-north-korean-hackers-over-wannacry-sony-cyberattacks
- Cisco named a “Champion” in Canalys Cybersecurity Leadership Matrix 2019” White Paper
- White Paper: Open platforms and the impact of Security Technologies, Initiatives, and Deployment Practices – Bill Jacob and Vincent Zimmer
- https://www.bloomberg.com/news/features/2018-10-04/the-big-hack-how-china-used-a- tiny-chip-to-infiltrate-america-s-top-companies
- https://krebsonsecurity.com/2019/06/tracing-the-supply-chain-attack-on-android-2/
- Secure Boot: An Effective, Low Risk Alternative to Commercial Solutions 13. Cisco Trustworthy Solutions
- Cisco Trust Anchor Technologies: Cisco Data sheet
Leave a Comment